Ensuring Safe, Compliant, and Trustworthy AI Interactions
We implement comprehensive guardrail systems and policy compliance layers that ensure your RAG applications generate accurate, safe, and compliant responses. Our solutions prevent hallucinations, enforce organizational policies, and maintain regulatory compliance across all AI-generated content.
Guardrail Architecture Framework
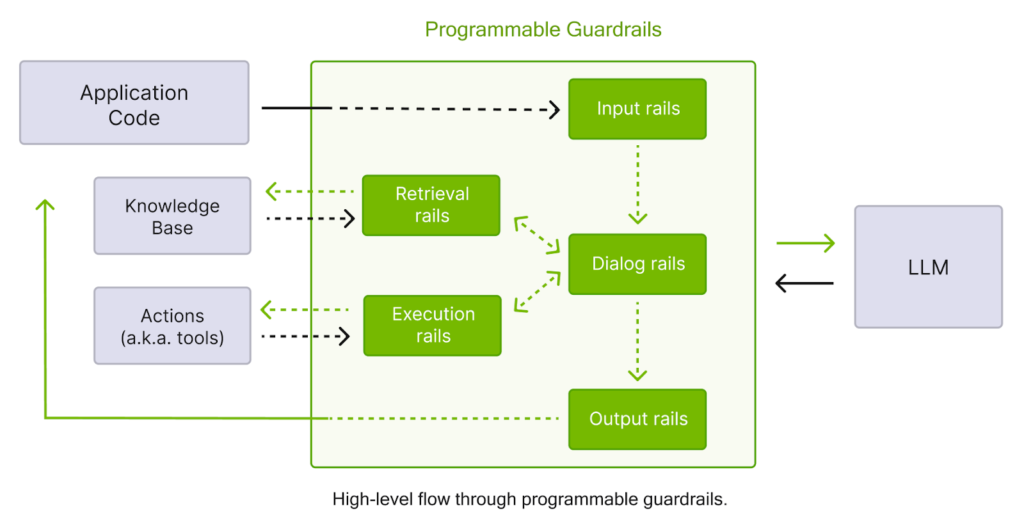
Multi-Layer Protection System
Defense-in-Depth Architecture
User Input → Input Validation → Context Retrieval → Response Generation → Output Filtering → Final Response
↓ ↓ ↓ ↓ ↓ ↓
Toxicity Check Policy Filter Source Validation Hallucination Prevention Compliance Check Audit LoggingCore Guardrail Components
| Component | Purpose | Implementation Level |
|---|---|---|
| Input Guardrails | Validate and sanitize user queries | Pre-processing |
| Context Guardrails | Ensure retrieved information quality | Retrieval phase |
| Generation Guardrails | Control LLM output generation | Generation phase |
| Output Guardrails | Filter and validate final responses | Post-processing |
| Audit Guardrails | Log and monitor all interactions | Entire pipeline |
Compliance & Safety Layers
1. Input Validation & Sanitization
Content Safety Filters
- Toxicity Detection: Identify harmful, offensive, or inappropriate language
- Prompt Injection Prevention: Detect and block adversarial prompts
- PII Detection: Identify and redact personally identifiable information
- Sensitive Topic Flagging: Mark queries about restricted subjects
Policy Enforcement
- Domain Boundary Checks: Ensure queries stay within authorized topics
- Usage Policy Validation: Verify query compliance with terms of service
- Jurisdictional Compliance: Apply region-specific restrictions
- User Permission Verification: Check user authorization for sensitive topics
2. Context Quality Assurance
Retrieval Validation
- Source Credibility Scoring: Weight responses by source reliability
- Recency Validation: Prioritize current information for time-sensitive topics
- Authority Verification: Check author/source credentials for specialized topics
- Contradiction Detection: Identify conflicting information in retrieved contexts
Context Augmentation
- Fact-Checking Signals: Append verification markers to retrieved content
- Confidence Scoring: Assign reliability scores to each retrieved chunk
- Metadata Enrichment: Add source credibility and timestamps to context
- Bias Detection: Identify potential biases in source material
3. Generation Control & Hallucination Prevention
Constrained Generation Techniques
- Prompt Engineering: Structured prompts that emphasize source grounding
- Template Enforcement: Force responses into approved formats
- Citation Requirements: Mandate source attribution in responses
- Uncertainty Expression: Require qualifiers for low-confidence information
Hallucination Prevention
- Faithfulness Scoring: Measure response alignment with source context
- Self-Consistency Checks: Verify internal consistency of generated responses
- Claim Verification: Cross-reference generated statements with sources
- Contradiction Prevention: Detect and correct conflicting information
4. Output Filtering & Validation
Content Safety Screening
- Moderation API Integration: Leverage advanced content moderation services
- Custom Rule Engine: Implement organization-specific content policies
- Tone Adjustment: Ensure appropriate language for different audiences
- Sensitive Content Redaction: Remove unauthorized information
Compliance Verification
- Regulatory Compliance Checks: Ensure adherence to industry regulations
- Legal Disclaimer Injection: Add required disclaimers to responses
- Access Control Enforcement: Filter content based on user permissions
- Export Control Screening: Prevent sharing of restricted technical information
Industry-Specific Compliance Solutions
Healthcare & Life Sciences
HIPAA Compliance Guardrails
- PHI detection and redaction
- Medical advice disclaimer requirements
- Clinical guideline adherence verification
- Patient safety protocol enforcement
Medical Accuracy Controls
- Evidence-based response requirements
- Peer-reviewed source prioritization
- Treatment recommendation restrictions
- Off-label use disclosure requirements
Financial Services
Financial Regulation Compliance
- FINRA/SEC communication rules
- Investment advice disclaimers
- Risk disclosure requirements
- Financial promotion regulations
Data Security & Privacy
- Financial data protection protocols
- Transaction security restrictions
- Client confidentiality enforcement
- Insider trading prevention measures
Legal & Professional Services
Legal Practice Guardrails
- Unauthorized practice of law prevention
- Attorney-client privilege protection
- Legal disclaimer requirements
- Jurisdiction-specific rule compliance
Confidentiality Controls
- Client matter confidentiality
- Privileged information protection
- Conflict of interest detection
- Document security protocols
Government & Public Sector
Public Information Compliance
- FOIA response guidelines
- Official communication protocols
- Public record handling rules
- Transparency requirements
Security Classifications
- Classification level enforcement
- Need-to-know access controls
- Secure information handling
- Audit trail requirements
Technical Implementation
Guardrail Integration Architecture
Modular Guardrail Framework
API Gateway → Guardrail Orchestrator → Individual Guardrail Modules → Response Aggregator
↓ ↓ ↓ ↓
Request Entry Route to Specific Execute Safety Checks Combine Results & Apply
Guardrail Services Based on Context Enforcement ActionsGuardrail Service Components
- Rule Engine: Policy rule evaluation and enforcement
- ML Classifiers: AI-powered content analysis
- Pattern Matchers: Regex and pattern-based detection
- External APIs: Integration with specialized moderation services
Performance-Optimized Implementation
Efficiency Strategies
- Cascade Evaluation: Apply cheap checks before expensive ones
- Early Termination: Stop processing when critical violations detected
- Parallel Processing: Run independent guardrails concurrently
- Result Caching: Cache frequent query/response validations
Latency Management
- Target: <200ms additional latency for guardrail processing
- Async processing for non-critical guardrails
- Progressive disclosure of intensive checks
- Performance monitoring and optimization
Policy Management System
Centralized Policy Configuration
Policy Definition Interface
- Visual policy rule builder
- Natural language policy specification
- Import/export of policy configurations
- Version control and change tracking
Policy Components
Policy = Conditions + Actions + Exceptions + Escalations
↓ ↓ ↓ ↓ ↓
Rule Set When to Apply What to Do Override Cases Alert ProceduresDynamic Policy Application
Context-Aware Policy Selection
- User role-based policy application
- Geographic policy variation
- Time-based policy adjustments
- Conversation context policy adaptation
Policy Testing & Validation
- Sandbox environment for policy testing
- A/B testing of policy variations
- Impact analysis before deployment
- Rollback capabilities for policy changes
Monitoring & Analytics
Real-Time Guardrail Monitoring
Dashboard Metrics
- Guardrail trigger rates and patterns
- Policy violation trends
- False positive/negative analysis
- Performance impact tracking
Alerting System
- Critical policy violation alerts
- Suspicious pattern detection
- System bypass attempts
- Performance degradation warnings
Compliance Reporting
Automated Compliance Reports
- Regulatory compliance certification
- Audit trail generation
- Policy adherence statistics
- Incident reports and resolutions
Analytics & Insights
- Risk assessment analytics
- Policy effectiveness measurement
- User behavior analysis
- Guardrail optimization recommendations
Advanced Features
Adaptive Guardrail Systems
Machine Learning Enhancement
- Anomaly detection for novel attack patterns
- User behavior analysis for personalized safety
- Continuous learning from false positives/negatives
- Predictive policy adjustment
Self-Improving Systems
- Feedback loop integration from human reviewers
- Automatic policy refinement based on outcomes
- Performance optimization through A/B testing
- Cross-organization learning (where appropriate)
Custom Guardrail Development
Specialized Guardrail Creation
- Domain-specific content classifiers
- Organization-unique policy enforcement
- Custom compliance requirement implementation
- Proprietary safety algorithm integration
Integration Flexibility
- Support for multiple LLM providers
- Compatibility with various RAG architectures
- Cloud, on-premise, and hybrid deployments
- Scalable from pilot to enterprise deployment
Implementation Process
Phase 1: Assessment & Design (2-3 Weeks)
Requirements Gathering
- Regulatory compliance analysis
- Organizational policy review
- Risk assessment and threat modeling
- Use case prioritization
Architecture Design
- Guardrail strategy development
- Policy framework design
- Integration architecture planning
- Success metrics definition
Phase 2: Core Implementation (4-6 Weeks)
Foundation Development
- Basic safety guardrail implementation
- Essential compliance checks
- Monitoring and logging framework
- Administrative interface development
Policy Configuration
- Core policy rule definition
- User role and permission setup
- Alert and escalation configuration
- Testing framework implementation
Phase 3: Enhancement & Optimization (Ongoing)
Advanced Features
- Machine learning enhancements
- Custom guardrail development
- Performance optimization
- Advanced analytics implementation
Continuous Improvement
- Regular policy reviews and updates
- Performance monitoring and tuning
- User feedback incorporation
- Emerging threat adaptation
Security & Privacy
Data Protection
- End-to-end encryption for sensitive validations
- Privacy-preserving content analysis techniques
- Secure audit log storage and access controls
- Compliance with data residency requirements
System Security
- Secure API authentication and authorization
- Rate limiting and abuse prevention
- DDoS protection and resilience
- Regular security audits and penetration testing
Success Metrics & KPIs
Safety & Compliance Metrics
- Hallucination Rate: <2% of responses containing unsupported claims
- Policy Violation Rate: <0.5% of interactions requiring intervention
- False Positive Rate: <5% of legitimate content incorrectly blocked
- Compliance Score: 99%+ adherence to configured policies
Performance Metrics
- Guardrail Latency: <200ms additional processing time
- System Uptime: 99.9% availability for critical guardrails
- Throughput: Support for 1000+ concurrent validations
- Resource Efficiency: <10% additional infrastructure cost
Business Impact Metrics
- Risk Reduction: Measurable decrease in compliance incidents
- User Trust: Increased user satisfaction and engagement
- Operational Efficiency: Reduced manual review workload
- Compliance Cost: Lower audit and remediation expenses
Support & Maintenance
Ongoing Management
- 24/7 monitoring and incident response
- Regular policy updates for changing regulations
- Performance optimization and scaling
- Security updates and vulnerability management
Training & Enablement
- Administrator training programs
- Policy management best practices
- Incident response procedures
- Regular knowledge sharing sessions
Our LLM Guardrail & Policy Compliance Integration provides the essential safety net for enterprise AI deployments, enabling organizations to leverage the power of RAG systems while maintaining control, compliance, and trustworthiness across every interaction.